The Concept of a Knowledge Worker
Category: information technology
Main Categories of an In-Depth Cybersecurity Policy
In 200 or more words for each answer, respond to the following:
What are the main categories of an in-depth cybersecurity policy?
How would a well-designed cybersecurity policy program help secure a government agency, such as the Department of Homeland Security (DHS)?
What are some challenges to making sure everyone in an organization follows the cybersecurity policy?
Role of Cybersecurity Policy in Securing Organizations and National Infrastructure
Using the Internet and/or the Library, research, and complete the following:
In a minimum of 1,000 words, explain the role cybersecurity policy plays in securing private organizations, public organizations, government organizations, and the nations infrastructure.
Current Trends in Telecommunications: The Rise of 5G Technology
Research and select a current trend in the area of telecommunications. Prepare a 10-15 page paper in Microsoft Word (counts as 11% of the final grade) AMU approved APA format (see Writing@APUS in the Resources Center) (350 words per page). At a minimum include the following:
Detailed description of the area researched
Technology involved in the area
Future trends in the area
Example companies involved in the area
Regulatory issues surrounding the area
Global implications for the area
Buyer Persona for Good Edi
Scenario
You are assigned to create a buyer persona for business using at least ten (10) segmentation variables (demographics, geographics, psychographics and behavioural
elements).
Your business, Good Edi (www.good-edi.com), may target more than one market, and if so, focus on what you think is the largest target market.
A buyer persona is a description of an individual from a specific segment. It assists marketers in creating marketing strategies, whether a new promotion, a new product, a new pricing strategy or any strategic marketing tactic.
Your buyer persona must include:
– Name, picture of the buyer, DOB, profession and income of the buyer.
– Bio of the buyer.
– Brand preferences.
– Communication channels utilised.
– Aspirations, lifestyle.
– Any additional factor that you find relevant to the brand of your choice.
The Importance of Computer Networks in the Digital Age
In your initial post, address the following:
First, introduce yourself. Tell us who you are, the program you are in at SNHU, and what you hope to gain by taking this course.
Describe your experiences with setting up a computer network, including experiences at home as well as in the workplace. If you do not have any experience building a network, write instead about your experiences using a network. This may range from using social media on a laptop or phone to sending a print job for a course assignment or for work. You may connect to a network at home, a coffee shop, the airport, work, or myriad other places.
You may want to trace your connections to networks during the span of one to three days. It can be surprising to find how much of our experience is networked these days. This will also suggest why this course is so important.
In response to two of your peers, extend the conversation.
Security Trade-offs: On-Premise vs. Cloud Computing
From: Ima Hacker, Chief Security Officer
To: You
Re: Lost in the clouds?
I am up in arms that we might be considering changing our enterprise architecture by moving our systems from our site to a commercial cloud vendor. Now that I’ve brought it up, Borden wants background (he knows what cloud computing is). Can you draft me a memo that lays out the security trade-offs among our current site architecture and the principle cloud options we might consider?
Trade-offs: Open Source vs. Commercial Office Software
From: Candace B. Rittenoff, Chief Financial Officer
To: You
Re: Money for nothing?
I am wondering why we are paying six figures to Microsoft each year when there are open source alternatives to Exchange Server and MS-Office.
What are the trade-offs between open source and commercial officing software? Is open source actually free? If not, how do we cost it against commercial software? What factors other than price should we be considering? Memo, please.
Bring Your Own Device (BYOD) Policy Considerations
From: Donatello Nobatti, Technical Director
To: You
Re: On the sly
Lotta B. Essen, our MicroSoft sales rep has been pushing unified communications solutions and telling me that BYOD is the next big wave. I’m not convinced but don’t have enough information. What are the considerations (pro and con) for moving forward with a BYOD plan (what are the best practices in developing a policy or do we just do chaos)? What are other firms doing to get this beast under control? Can you give me a memo on this?
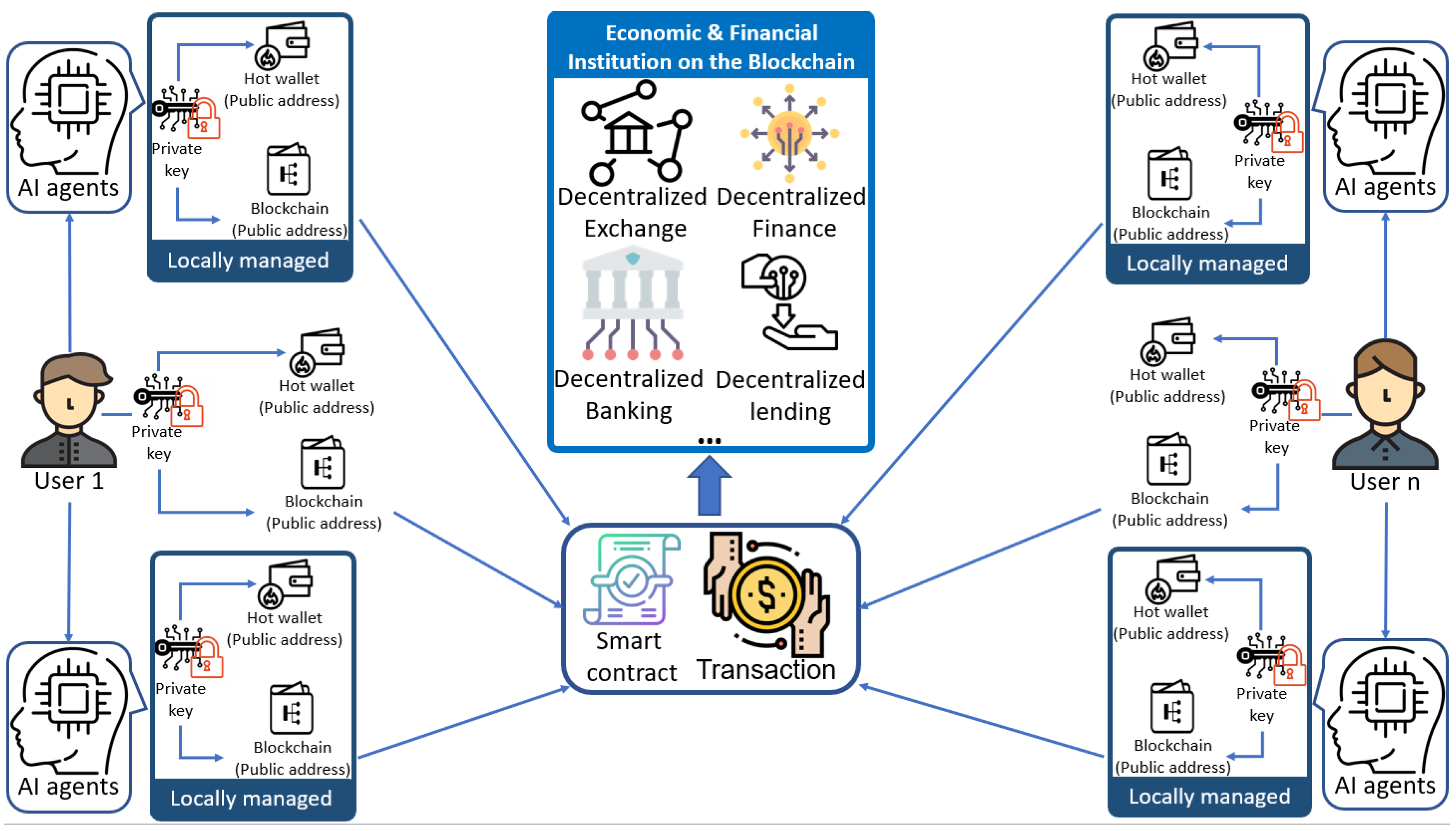
Blockchain as an Enabler for Autonomous Agents
Blockchain as an Enabler for Autonomous Agents
Using mentor or model texts is a strategy to improve your own writing. The New York Times describes mentor texts as, “Demystifying the writing process via examples students can learn from and emulate.” In this assignment, you will locate a mentor text in the form of a dissertation that may or may not be similar to your own topic to use as a model while you write your chapter 2. It is most helpful to find a dissertation with a literature review similar to your own, but if that is not possible, you may look for the next best option.
Directions:
Use ProQuest Dissertations & Theses Global database on the UC Library website to locate mentor text dissertation (preferably it would be related to your topic). Topic: Blockchain as an Enabler for Autonomous Agents
You may need to use advanced search options to help narrow your search.
Scan read the entire dissertation.
Carefully read the literature review section.
Provide a one-paragraph summary of the entire literature review.
Write a second paragraph about what you learned through reviewing chapter 2.
Additional Information:
ProQuest Dissertations & Theses Global database is accessible through the Databases link below the blue picture on the Library website. The Databases tab will access an alphabetical list of the Library databases. The dissertation database is listed twice, as Dissertations and Theses and as ProQuest Dissertations and Theses.